merkle root
What Is a Merkle Root?
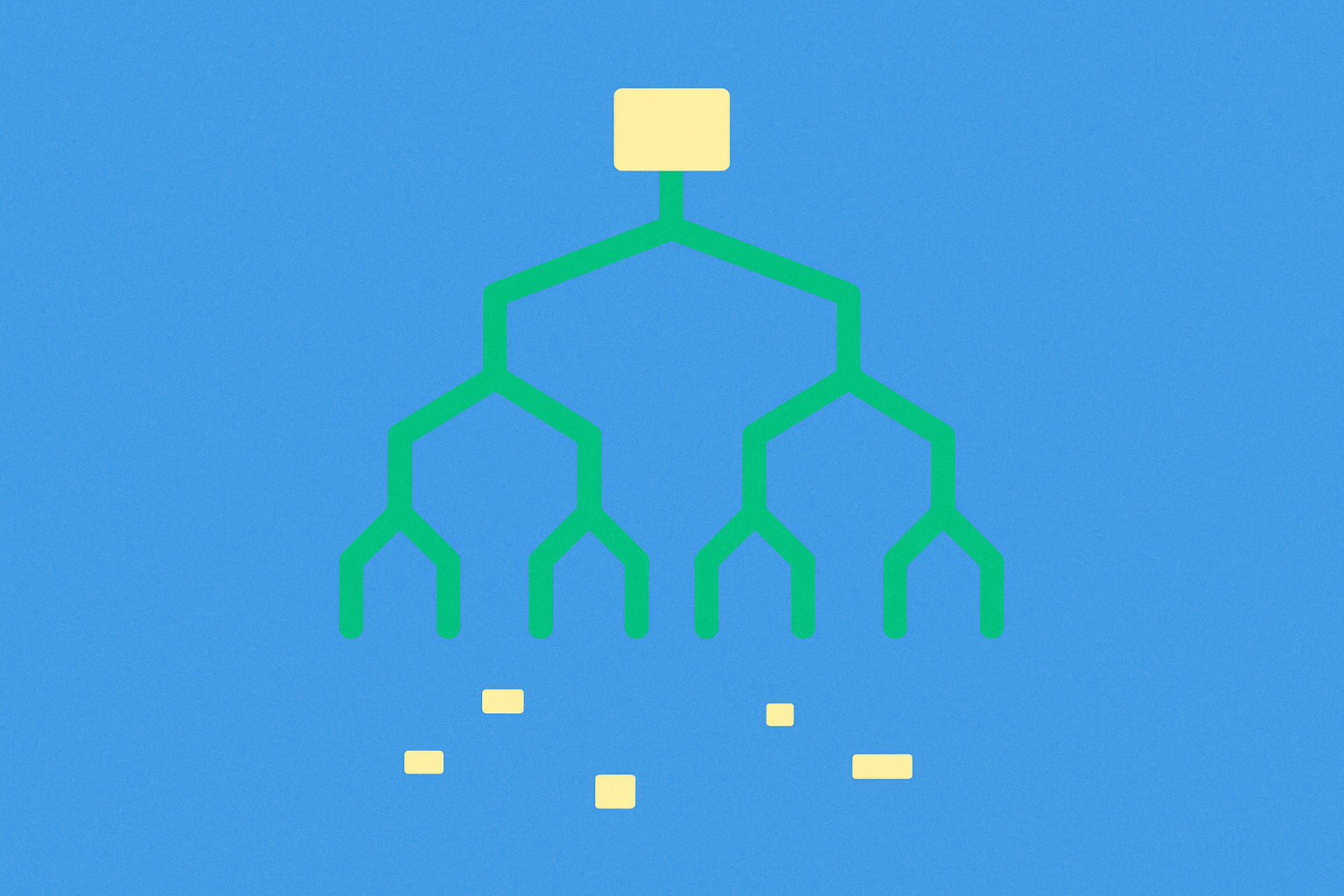
A Merkle root is a single hash that summarizes all transactions within a block, created by recursively combining transaction hashes in a tree-like structure. This hash is stored in the block header and serves as a compact summary of which transactions are included in the block.
Here, a “hash function” refers to an algorithm that compresses arbitrary data into a fixed-length fingerprint. The “block header” is a segment of metadata containing elements such as the timestamp, the hash of the previous block, and the Merkle root, which helps the network quickly verify blocks.
Why Is the Merkle Root Important in Blockchain?
The Merkle root is crucial because it enables users to verify whether a transaction is included in a block without downloading all transactions in that block. Only a small amount of data is needed for verification, making it possible for light nodes—clients that download only block headers—and mobile wallets to operate securely with limited resources.
In Bitcoin, SPV (Simplified Payment Verification) relies on the Merkle root. Wallets download the block header and use a short “proof path” to compare against the Merkle root, determining whether a transaction is included. For blocks containing thousands of transactions, this significantly reduces bandwidth and storage requirements.
According to public block explorer statistics, most Bitcoin blocks typically include about 1,000 to 3,000 transactions as of 2025 (source: mempool.space, 2025-10). At this scale, the efficiency gains from using Merkle roots are especially pronounced.
How Is a Merkle Root Calculated?
Calculating the Merkle root involves merging transaction hashes upwards in a Merkle tree until only one hash remains.
Step 1: Compute the transaction hash for each transaction. A transaction hash is a fixed-length fingerprint generated by hashing the transaction data.
Step 2: Pair adjacent transaction hashes, concatenate them, and hash the result to form their parent node’s hash. Continue merging in pairs to build the next layer.
Step 3: If a layer has an odd number of hashes (as in Bitcoin), duplicate the last hash to complete the pairing—details may vary across blockchains.
Step 4: Repeat this process until only one hash remains at the top. This final hash is the Merkle root. In Bitcoin, intermediate results often use double hashing (applying the hash function twice) for added resistance against collision and length-extension attacks.
What Is the Relationship Between Merkle Root and Merkle Tree?
A Merkle tree organizes large volumes of data as hashes in a hierarchical “binary tree.” Each leaf node is a transaction hash, and each parent node is a combined hash of its two child nodes. The Merkle root is the topmost parent hash of this tree—a summary representing all underlying data.
You can think of it like a folder: leaves are fingerprints of individual files, upper layers are fingerprints of subfolders, and the Merkle root is the overall fingerprint of the entire folder. If any leaf changes, all parent hashes up to the root change as well, making it a reliable indicator of whether the dataset has been altered.
How Is Merkle Root Used to Verify Transactions?
To verify if a transaction is included in a block, you reconstruct the “proof path” from that transaction up to the Merkle root and compare it with the Merkle root in the block header.
Step 1: Obtain the transaction hash, which can be copied from your wallet or from a block explorer’s transaction details page.
Step 2: Get the Merkle proof—block explorers typically provide a series of “path hashes” (sibling hashes adjacent to your transaction) for layered merging.
Step 3: Sequentially concatenate and hash your transaction hash with each path hash layer by layer until you reach the top-level hash.
Step 4: Compare your computed top-level hash with the block’s Merkle root. If they match, your transaction is confirmed as part of that block.
In practice—for example, during deposit processes on Gate—the confirmation page will display the block height and offer links to relevant block explorers. You can visit these pages, check the Merkle root in the block header, and use these steps for self-verification.
Differences Between Merkle Roots in Bitcoin and Ethereum
In Bitcoin, the Merkle root represents the top-level hash of a binary Merkle tree built from all transactions and is written into the “merkle root” field of the block header.
In Ethereum, block headers contain multiple roots: transactionsRoot (for transactions), stateRoot (for global state), and receiptsRoot (for receipts). These are built using “Merkle Patricia Trie” structures—a variant suited for key-value storage—enabling more complex state and indexing. Despite different implementations, they all serve to compress large datasets into verifiable digests.
The community continues to explore more efficient data structures—such as Verkle trees—to further reduce proof sizes and sync costs for light clients. Nevertheless, Merkle-based designs remain widely used for generating verifiable digests and proofs.
Risks and Misconceptions Associated with Using Merkle Roots
First, the Merkle root only proves “the integrity of a set”; it does not directly reveal which transactions are present. You need both a Merkle proof and transaction hash to confirm inclusion.
Second, SPV verification relies on trusting that received block headers are from the main chain. Network attacks (such as isolation by malicious nodes) could temporarily mislead users. For this reason, funds-related operations should wait for sufficient confirmations; exchanges like Gate require different numbers of confirmations per chain to mitigate double-spending and reorganization risks.
Third, implementation details differ across blockchains—such as merge order, handling odd leaves, hashing algorithms, and encoding formats. Errors in these processes can result in failed verifications.
Fourth, security depends on the collision resistance and tamper-proof nature of hash functions. While mainstream hash algorithms are widely used today, any vulnerability at the algorithmic level would directly undermine Merkle root reliability.
How Can Beginners View Merkle Roots in Tools?
Step 1: Enter your transaction hash in a block explorer, open its details page, find its corresponding block, and navigate to that block’s page.
Step 2: In the block page’s “block header” section, locate fields such as “merkle root” (Bitcoin) or “transactionsRoot/stateRoot/receiptsRoot” (Ethereum). These fields are the respective Merkle roots.
Step 3: If “Merkle Proof” or “proof path” is provided on the page, you can use earlier steps to calculate and compare with the Merkle root for transaction verification.
On Gate’s deposit records page, you can find your transaction’s block height and access the corresponding block explorer page to locate block header fields and further understand how Merkle roots function.
Summary: What Value Does Understanding Merkle Roots Bring?
Mastering Merkle roots helps you understand why blocks are trustworthy, how wallets perform lightweight verification, and how different public chains choose their data structures. By compressing numerous transactions or states into a single verifiable digest, Merkle roots boost efficiency while maintaining security boundaries. For beginners, knowing how to use Merkle roots and proof paths empowers you to confidently verify deposits, transfers, and on-chain interactions—and better evaluate confirmation counts and risks.
FAQ
Why Can Lightweight Wallets Verify Transactions Using Only the Merkle Root?
Lightweight wallets do not store all transaction data from every block. They only need to keep the Merkle root and proof path to verify whether a specific transaction has been tampered with—similar to checking just the barcode on a package rather than opening it to inspect its contents. This dramatically reduces storage and bandwidth requirements for mobile devices, enabling secure mobile wallets.
How Can Changing the Merkle Root Compromise an Entire Block?
The Merkle root acts as an “electronic fingerprint” for the whole block. Any tampering with even a single transaction changes its hash and consequently alters all parent hashes up to the Merkle root. This cascading effect allows all network nodes to instantly detect modifications. Such design underpins blockchain’s anti-tampering capability—a cornerstone of its security.
Why Use a Merkle Tree Instead of Concatenating All Transaction Hashes Directly?
Directly concatenating all transaction hashes would produce an unwieldy string that’s hard to store and compare. The binary hierarchy of a Merkle tree exponentially compresses complexity into one fixed-length root hash. This ensures efficient verification for any number of transactions without verification time increasing linearly with transaction count.
Can SPV Wallets Be Fooled by Relying on Merkle Roots for Verification?
Relying solely on one node’s provided Merkle root carries risk; however, SPV wallets typically request Merkle roots for the same block from multiple independent nodes for cross-checking. As long as most nodes are honest, forging a false Merkle root is extremely difficult. This pragmatic balance between performance and security suits everyday payment scenarios.
Why Must Miners Recalculate the Merkle Root During Mining?
Whenever miners select different combinations of transactions for inclusion in a new block, the Merkle root changes—which in turn alters the block header’s hash. Miners continuously adjust transaction order and nonce values searching for hashes that meet network difficulty requirements; throughout this process, recalculating the Merkle root is mandatory. This mechanism ensures miners genuinely process and validate transaction content.
Related Articles

The Future of Cross-Chain Bridges: Full-Chain Interoperability Becomes Inevitable, Liquidity Bridges Will Decline

Solana Need L2s And Appchains?
