Guide to Merkle Trees and Merkle Roots
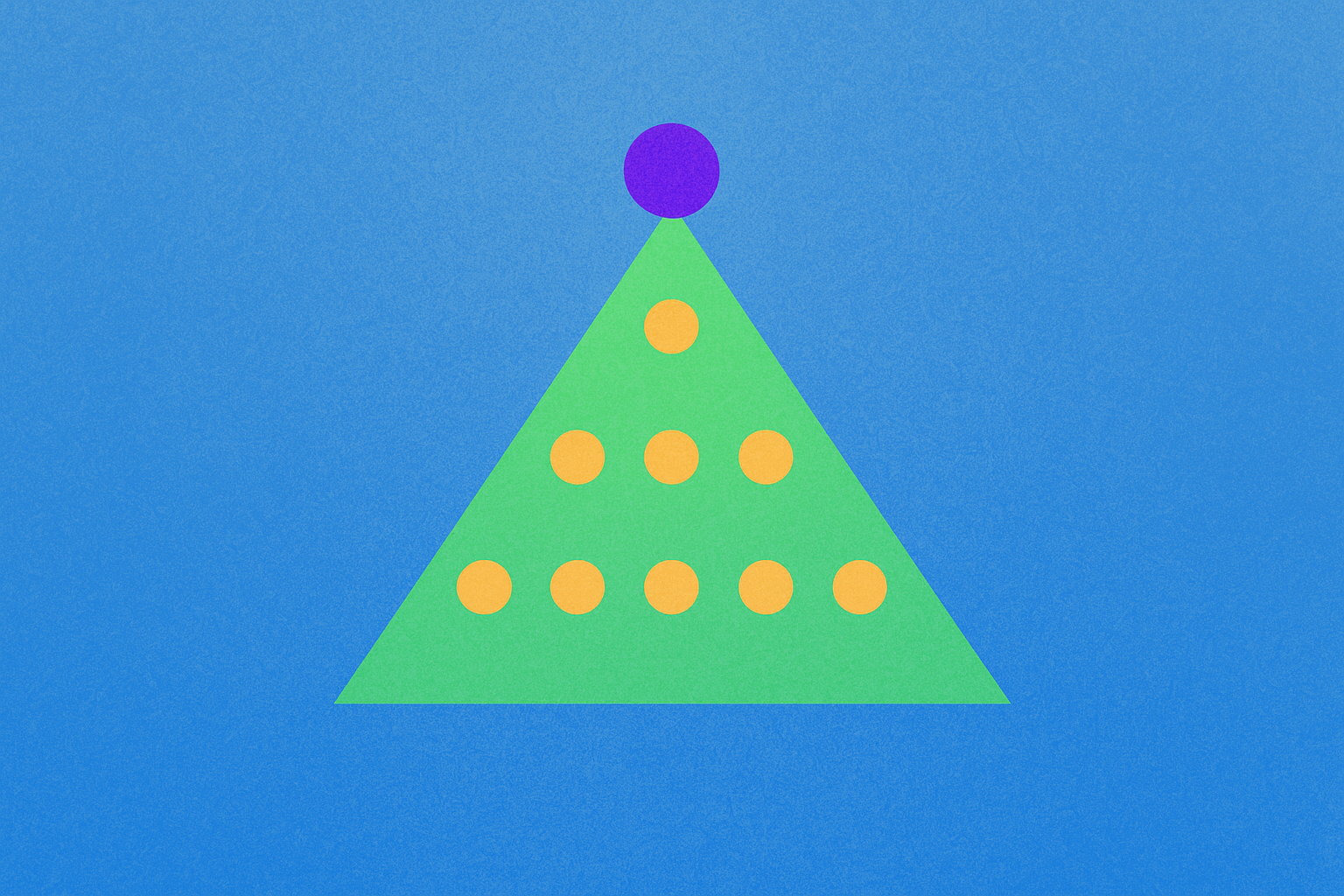
What is a Merkle Tree?
The concept of Merkle Tree was proposed in the early 1980s by Ralph Merkle, a computer scientist renowned for his groundbreaking work in public-key cryptography.
A Merkle Tree is a data structure used to efficiently verify the integrity of a large dataset. This structure is particularly valuable in peer-to-peer networks, where participants need to share and validate information independently without relying on a central authority.
Hash functions form the fundamental foundation of Merkle Tree structures. These cryptographic functions take input data of any size and produce a fixed-size output, making them essential for creating the hierarchical verification system that Merkle Trees provide.
How Do Merkle Trees Work?
Consider a scenario where you need to download a large file. With open-source software, you typically want to verify that the hash of the downloaded file matches the value published by the developers.
If the hashes do not match, you face a problem. Either you have downloaded a malicious file disguised as legitimate software, or the download was corrupted during transmission.
Merkle Trees simplify this verification process significantly. Your file can be divided into smaller chunks. For example, a 50 GB file could be split into one hundred parts, each with a size of 0.5 GB.
In this scenario, your source provides a hash known as the Merkle Root. This single hash represents all the data fragments that compose your file. Rather than comparing numerous individual hashes, you take each pair of hashes, combine them, and submit them together to the hash function. This process continues recursively until you obtain the Merkle Root (also called Root Hash) that represents the entire downloaded file.
If the Merkle Root matches the value provided by the source, the file is intact and unmodified. If they differ, you know that the data has been altered or corrupted.
Why Are Merkle Roots Used for Bitcoin?
Merkle Trees are essential to Bitcoin and numerous other cryptocurrencies. They are an integral component of every block and can be found embedded in block headers.
Mining Process
A Bitcoin block consists of two main parts: the Block Header (fixed-size metadata) and a list of transactions (variable-size data). Miners need to hash data repeatedly to produce an output that meets specific difficulty conditions. They modify a nonce value in the Block Header to generate different hash outputs until they find one that satisfies the network requirements.
A Merkle Root significantly simplifies this mining process. Instead of hashing an entire block containing thousands of transactions, miners construct a Merkle Tree from the transactions and insert the resulting root hash into the Block Header. Then they only need to hash the Block Header itself, rather than the complete block. This efficiency is crucial given the computational demands of the mining process.
Verification and Light Clients
Merkle Roots possess another valuable property for light clients—nodes that do not maintain a complete copy of the blockchain. These clients can simply request a Merkle Proof, which is cryptographic evidence that proves a specific transaction is included in a particular block. This process is known as Simplified Payment Verification (SPV).
With a Merkle Proof, you only need to perform hashing a small number of times rather than many. Since blocks contain thousands of transactions, using Merkle Proofs saves substantial time and computational resources, enabling users with limited hardware to participate in the network.
Final Considerations
Merkle Trees have proven to be extremely useful across numerous applications in computer science and distributed systems. In decentralized networks, Merkle Trees enable efficient verification of information without flooding the network with unnecessary data.
Without Merkle Trees and Merkle Roots, Bitcoin blocks and other cryptocurrency blocks would not be as compact as they are today. Merkle Proofs enable users to verify that transactions have been included in a block without overwhelming the network with excessive data requests. This elegant solution demonstrates how cryptographic innovations continue to be fundamental to the security and efficiency of blockchain technology.
FAQ
What is a Merkle Tree and what are its uses?
A Merkle Tree is a data structure that stores and verifies data block integrity through hash values. It enables efficient verification of entire datasets and is widely used in blockchain and cryptography for ensuring data authenticity and security.
How is the Merkle root calculated? What is its working principle?
Merkle root is computed by hashing data layer by layer. Start with leaf data, hash pairs of nodes upward, combining results until reaching a single 32-byte hash value at the top. This final hash is the Merkle root.
How are Merkle trees applied in blockchain?
Merkle trees verify transactions and ensure data integrity in blockchain by creating a hash structure. They enable efficient batch verification, reduce data storage, and enhance security through cryptographic hashing, making blockchain validation faster and more reliable.
What are the advantages of Merkle trees compared to other data structures?
Merkle trees efficiently verify data correctness and integrity while reducing memory requirements. They occupy significantly less disk space compared to other data structures, making them ideal for blockchain and distributed systems.
How to use Merkle trees to verify data integrity and authenticity?
Merkle trees verify data integrity by organizing data into a hierarchical hash structure. Any data change immediately alters the root hash, instantly detecting tampering. Verification requires only comparing the root hash with the Merkle path, enabling efficient validation without checking all data.

Công Nghệ Blockchain: Tìm Hiểu Hoạt Động Và Ứng Dụng
What Is Hashing?
What are nodes?

How to Mine Bitcoin for Free

How Does Pi Mining Work? Everything You Need to Know

Fact Check: Mining Bitcoin for Free
Is Bitcoin Dead? The Truth About Bitcoin's Survival

Bull and Bear Markets: What They Are and How They Differ

What is cross margin
The Difference Between the 2025 and 2021 Crypto Bull Runs

How to get free bitcoins







